Security Configuration
This document describes and guides how to configure security options for the eKYC flow on the FPT AI eKYC Portal. Some options will be enabled by default, while others will be disabled as they require coordination between FPT AI and customers for effective use. Customers should carefully review these options to consider using them appropriately according to their needs.
To access this page, you need to log into the eKYC Portal system, select language EN and choose the eKYC Settings tab in the left menu. Then, select Security in the submenu.
The main security options that can be applied for the eKYC flow include:
- Transmitting Data Encryption
- At-rest Data Encryption
- Transmitting Data Integrity Check
- Client UUID Authenticity Check
The Transmitting Data Integrity Check option is enabled by default and cannot be disabled, therefore customers do not need to configure it on the eKYC Portal.
1. Transmitting Data Encryption

-
Description:
- Transmission data encryption is an option to ensure the security and safety of data during transmission. This option will be disabled by default.
- The encryption method used by the system is hybrid encryption to ensure security and performance during data transmission between components. This mechanism combines two encryption algorithms: RSA (asymmetric) and AES-256 (symmetric), to leverage the strengths of both methods.
- AES-256 is used to encrypt the main data (payload), ensuring fast processing speed and high security for large data.
- RSA is used to encrypt the AES key (symmetric key), ensuring the session key can only be decrypted by the valid recipient.
-
Configuration: Use the toggle button to enable or disable this feature.
Customers using transmitting data encryption will not be able to retrieve data from the Proxy Server as it is encrypted (see documentation about Integration using Proxy Server). Customers will need to retrieve data and eKYC results through callback or the eKYC server's get_result API (see documentation Data retrieval methods).
2. At-rest Data Encryption

-
Description:
- At-rest data encryption is an option to ensure the security and safety of data during storage. This option will be disabled by default.
- The encryption method used is Server-Side Encryption with Customer-Provided Keys (SSE-C) with the eKYC system acting as the customer.
-
Configuration: Use the toggle button to enable or disable this feature.
The at-rest data encryption of the FPT AI eKYC system is provided by FPT Cloud's Object Storage service. Customers can refer to more about this method in the FPT Object Storage Encryption documentation.
3. Transmitting Data Integrity Check
- Description:
- Transmitting data integrity check is an option to ensure the security and safety of data during transmission. This option will be enabled by default and cannot be disabled.
- The verification mechanism is as follows:
- A secret code is hashed together with the transmitted data to create a hash token.
- This hash token is then sent along with the data from the client to the eKYC Server.
- The eKYC server will compare the received hash token with the hash token generated by the eKYC server using the same method as above. If the two hash tokens do not match, the transmitted data will be considered invalid and will not be processed.
Currently, this option is not applied to customers integrating through Web SDK or APIs but only applies to customers integrating through Mobile SDK.
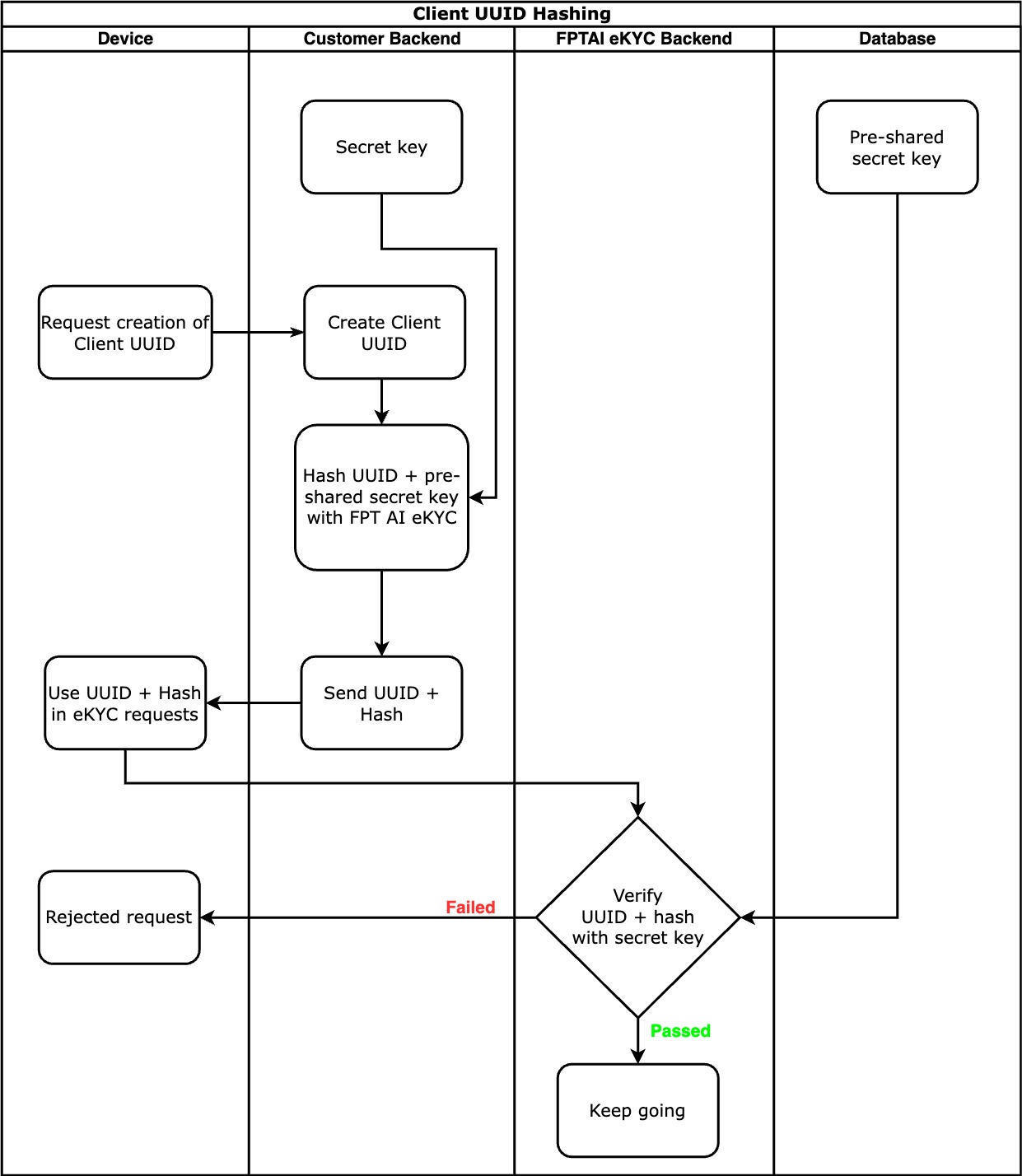
4. Client UUID Authenticity Check

- Description:
- Client UUID authentication check is an additional security mechanism (besides API key and token) to ensure that requests received by the eKYC system are indeed from the customer. This option will be disabled by default.
- The verification mechanism is as follows:
- Before initializing the eKYC flow, the client sends a request to create a Client UUID to the customer's server.
- The customer's server generates a Client UUID and hashes it together with a secret key configured on the eKYC Portal.
- The Client UUID and this hash token will then be sent along with the eKYC flow requests.
- The eKYC server will compare the received hash token with the hash token generated by the eKYC server using the same method as above. If the two hash tokens do not match, the request will be considered invalid and will not be processed.
- The verification mechanism flow is as follows:
- Configuration:
- Use the toggle button to enable or disable this feature.
- Enter the secret key in the
Pre-shared keyfield after enabling.
To ensure security when applying this option, customers need to build their own secure mechanism to send and receive Client UUID from server to client and ensure confidentiality in the Client UUID generation method on the server.
- Make sure to click the
Updatebutton after making changes to apply the new configuration. - If you encounter any issues, please contact technical support.